_______________ Best Describes Authentication That Requires Two or More Factors
Which of the following statements best describes authentication server logs. Dual-factor authentication means using two independent authentication methods such as a token card and usernamepassword combination whereas multifactor authentication can mean two or more methods of establishing identity.

What Is Two Factor Authentication 2fa Defined Explained
The term multi-factor has been used to describe any authentication process requiring two or more.

. Match the type of authentication factor with its description. Determines what a security principal can do after being authenticated. Which two factors influence the type of SOP used.
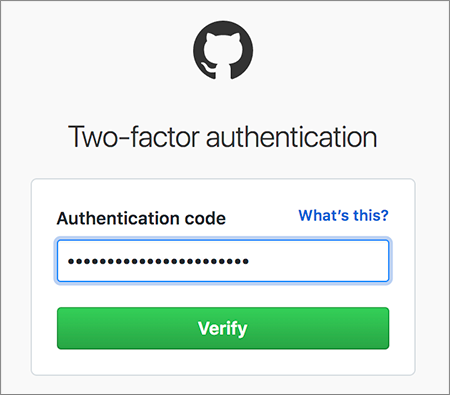
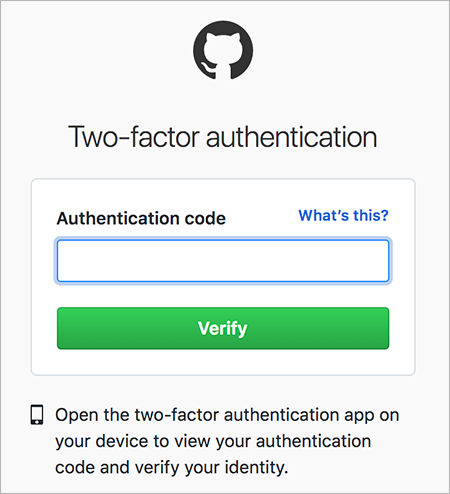
Two-factor authentication 2FA sometimes referred to as two-step verification or dual-factor authentication is a security process in which users provide two different authentication factors to verify themselves. Therefore passwords and PINs are examples of authentication. By definition true multifactor authentication requires the use of solutions from two or more of the three categories of factors.
The phrases below describe types of authentication factors. Requires the use of two of the three authentication factors. Hand-in-hand with MFA are time-sensitive one-time passwords.
Two-factor authentication 2FA usually combines a knowledge factor with either a biometric factor or a possession factor such as a security token or key. Is a security technology that requires at least two authentication methods from different types of credentials to verify a users. What the user has such as a security token.
Would not constitute multifactor authentication The three categories of factors from which two or more are required to be true multifactor authentication are. Something the user is. Using multiple solutions from the same category.
Multifactor authentication combines two or more authentication methods requiring a user to supply multiple credentials. Contains user accounts and their associated passwords in a workgroup model. An object containing a base secret like the magnetic stripe on a cash card.
2FA is implemented to better protect both a users credentials and the resources the user can access. Learn more about how multi-factor authentication ensures the protection of computing systems in the face of. It uses the RSA public-key signature based algorithm on integers with large prime factors B.
It requires two measurements of hand geometry C. Authentication server logs capture user group and administrative activity. Answer B is incorrect because two-factor authentication requires two of the three primary categories of authentication to be used.
Multifactor authentication MFA is a security technology that requires multiple methods of authentication from independent categories of credentials to verify a users identity for a login or other transaction. 275 Which of the following is true of two-factor authentication. It relies on two independent proofs of identity.
Two-factor authentication is considered more secure than single-factor authentication. Multifactor authentication combines two or more independent credentials. I would suggest multi-factor authentication which is a high-assurance approach that verifies users using multiple system-independent factors.
It does not use single sign-on technology D. MFA like 2FA confirms user identity by using biometrics device-based confirmation additional passwords and even location or behavior-based information eg keystroke pattern or typing speed. Memorized information like a password.
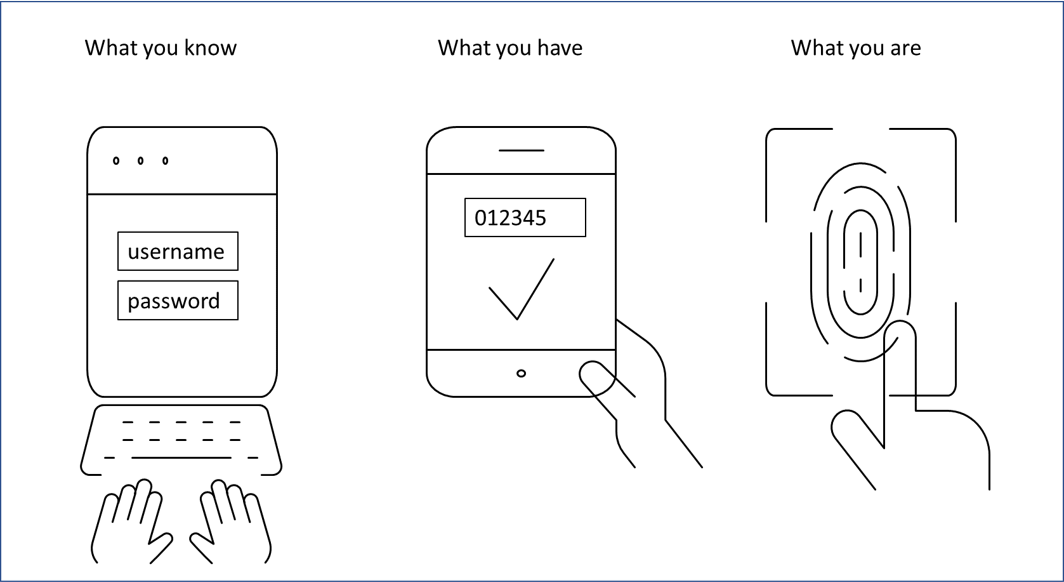
Three-factor authentication requires all three categories. There are three common factors used for authentication. -- from the user.
Strong authentication though not officially defined is often used to describe an authentication process that requires two or more authentication factors of different kinds -- knowledge location possession etc. Single-factor authentication B C and D are incorrect. What the user knows such as a password.
Two-factor authentication 2FA sometimes referred to as two-step verification or dual-factor authentication is a security process in which users provide two different authentication factors to verify themselves. Therefore this is an example of authentication. This method allows the user to obtain exclusive access to a password that will only work for a short amount of time making it useless to steal after that period has expired.
While one authentication factor may be hackable its exponentially harder to hack two or more. Answer B is incorrect because two-factor authentication requires two of the three primary categories of authentication to be used. Which of the following terms best describes authentication that requires two or more factors.
This process is done to better protect both the users credentials and the resources the user can access. Represents the way that security principals prove their identity. Quasifactor authentication is not an industry-standard term.
Encompassing authentication or 2fa along with similar terms is an electronic authentication method in which a user is granted access to a website or application only after successfully presenting two or more pieces of evidence or factors to an authentication mechanism. Two-factor authentication is considered more secure than single-factor authentication because the individual who wants to gain access must possess two items to be successful. Something you know such as a password Something you have such as a smart card Something you are such as a fingerprint or other biometric method Identification occurs when a user professes an identity such as with a username and authentication occurs when users prove their identity.
Today a typical enterprise runs with multiple assets. This reduces the likelihood that an intruder would be able to successfully impersonate a user during the authentication process. Passwords became a de facto standard for online.
Multi-factor Authentication MFA is an authentication method that requires the user to provide two or more verification factors to gain access to a resource such as an application online account or a VPN.

Explore Multi Factor Authentication And Ssl Certificates Unit

2022 Comptia Security Sy0 601 Best Exam Study By Brian Macfarlane Flashcards Quizlet

Nist Authentication Basics And Azure Active Directory Microsoft Docs
Multi Factor Authentication Article Khan Academy

Multi Factor Authentication For Developers Fusionauth

What Is Two Factor Authentication 2fa Defined Explained

Authentication Factor An Overview Sciencedirect Topics

Multi Factor Authentication Article Khan Academy

What Is The Best Description Of Two Factor Authentication How To Discuss
Tech Brief Multifactor Authentication With Citrix Nfactor

What Are The Three Authentication Factors Rublon

What Is Two Step Verification How Does It Work

Multi Factor Authentication For Developers Fusionauth

Osi Model The 7 Layers Of Network Architecture Bmc Software Blogs
Multi Factor Authentication Article Khan Academy



Comments
Post a Comment